Predict
Deep Learning Analysis stops attacks pre-execution
Our Managed Security Operations Center (SOC) provides the necessary synergy between people, process, and technology to deliver world-class cybersecurity protection without the need to staff, train and maintain your own SOC.
Deep Learning Analysis stops attacks pre-execution
Automatic remediation of threats at the endpoint
Comprehensive monitoring and alert escalation
Customized incident response plans and support
Powerful and practical cybersecurity requires a defense-in-depth approach.
Our Managed SOC solution considers every attack vector and attack surface within your IT infrastructure.
Your infrastructure is monitored and protected 24/7 by a fully staffed team of cybersecurity experts.
Security Information and Event Management provides intelligence, greater visibility and aggregation of events across your network.
Managed endpoint protection platform powered by deep learning for zero-time prevention.
Managed threat detection and response (MDR) to defend your entire IT environment.
Monitor malicious activity within your network and endpoints.
Monitor network traffic for early threat detection and a swift response.
Avoid attacks by identifying your network’s vulnerable systems.
Proactively guard your critical business infrastructure with a team that understands adversary tactics and techniques.
Our security operations center (SOC) works around the clock monitoring your network more effectively thanks to the Security Orchestration and Automated Response (SOAR) capabilities of our platform. As a result, you get wide-reaching security coverage, defense-in-depth controls, and experts as an extension of your team.
![]()
Continuously predict, prevent, detect, and respond to advanced threats efficiently and effectively by combining deep learning-enabled technology and a team of cybersecurity experts providing 24/7 monitoring, analysis, and incident response.
Our managed platform approach to cybersecurity simplifies operations and reduces security gaps left by traditional IT security tools. Compromised login credentials are found in over 80% of all network intrusions where traditional tools provide limited visibility and protection. We leverage machine learning to trigger detailed and actionable alerts in real time when abnormal behavior occurs that could signal a data breach, including compromised credentials, lateral movement, and insider threats.
Already in Your Network, today’s Advanced Persistent Threats (APTs) are prompting IT departments to upgrade monitoring, protection, and incident response activities, to avoid the expense and embarrassment of a data breach. Endpoint detection and response (EDR) provides a response beyond legacy anti-virus for an endpoint security solution that is integrated, powerful, and includes remediation capabilities. Netsurion’s 24/7 managed threat protection solution safeguards your endpoints from ransomware and other advanced persistent threats.
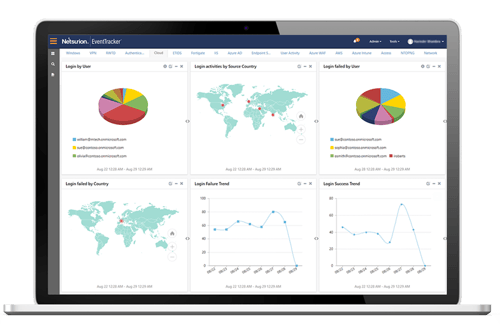
Your Microsoft 365 SaaS applications are mission-critical. User productivity and effectiveness depend on Azure Active Directory (AD), Microsoft Exchange, SharePoint Online, OneDrive for Business, and Microsoft Teams. In cooperation with Microsoft, we restore visibility to user, application, and data behavior through audit/logging, PowerShell activity tracking, and a 24/7 SOC to detect and escalate incidents. We alert you to Microsoft 365 security problems and recommend mitigation steps long before any downtime occurs.
As employees move from a trusted enterprise network to home offices, protecting assets and data has never been more challenging. Security gaps increase with remote access to corporate servers, to VPNs (virtual public networks), or personal networks. Cyber criminals are aggressively targeting you and your employees for financial gain. Remote Workforce Threat Detection from Netsurion protects sensitive data that’s outside your company network to fill cybersecurity gaps.

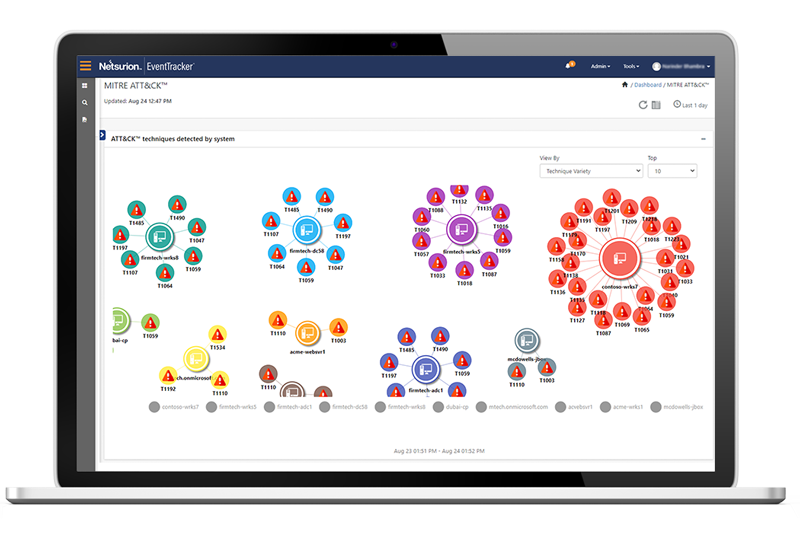
Threats are dynamic and attack vectors change constantly. We ensure you can respond quickly and minimize damage by using the rich context enabled by actionable threat intelligence. Our Threat Center portal easily incorporates threat intelligence from the MITRE ATT&CK framework, commercial and open source threat feeds, and security analysts who focus on emerging threats across the internet. Our intuitive reports and recommendations ensure that cyber threat intelligence (CTI) is actionable and tailored to your organization and customers.
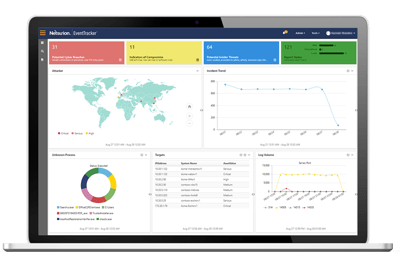
Uncover the cyber threat intelligence hidden in your log data that helps you identify actual threats and risks to your data and assets. SIEM begins with the collection, standardization, and storage of security event data, and then uses an array of analytical methods to examine, report, and act upon security alerts pulled from that data in real time.
SIEM and log management capabilities provide the core of our threat protection platform, and empower threat detection with support for thousands of devices and applications and over 2,000 out-of-the-box reports.
Our SIEM platform is tasked with monitoring an ever-increasing attack surface that encompasses physical servers, workstations, endpoints, and cloud infrastructure to ensure your environment is safe.
Rule-based alerts are set and backed by dashboards, alert scores, contextualization, and automated response capabilities to ensure your organization quickly responds to any alarming anomalies or threats.
![]()
SIEM can help your organization reduce risk and improve operational efficiency by automating the steps required by various industry regulations and mandates. With our combined SIEM, log management, and SOC capabilities, organizations can secure the environment, establish the baseline, track user activity, alert on potential violations, and generate audit-ready reports to help with PCI DSS, HIPAA, ISO 27001, NIST 800-171, DoD, RMF, GDPR, and other compliance requirements.